これをやるには最初のカウントの際に “as” を利用して別名をつけてあげるとうまくいきます。
SPLの書き方
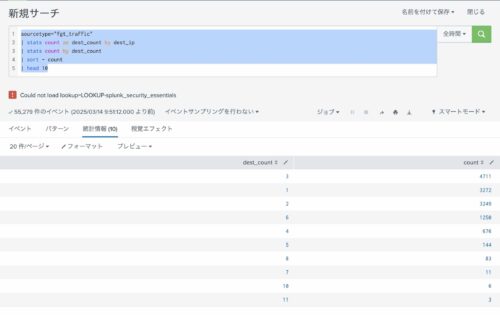
下記のSPLは、SPLの例です。
sourcetype="fgt_traffic"
| stats count as dest_count by dest_ip
| stats count by dest_count
| sort - count
| head 10
実際に実行するとこうなります。
WHY DON'T YOU DO YOUR BEST!!
これをやるには最初のカウントの際に “as” を利用して別名をつけてあげるとうまくいきます。
下記のSPLは、SPLの例です。
sourcetype="fgt_traffic"
| stats count as dest_count by dest_ip
| stats count by dest_count
| sort - count
| head 10
実際に実行するとこうなります。

bucket もしくは bin を利用して _tme を指定した時間の幅に分割した後、stats マクロを使用しすれば、その時間の幅毎に特定の項目の出現回数を表示させることができます。
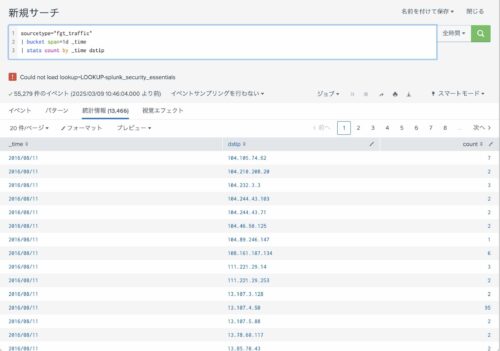
下記のSPLは、ログデータを1時間毎に分割し、それぞれの時間内での dstip(通信先)毎の出現回数をカウントし表示させるSPLの例です。
sourcetype="fgt_traffic"
| bucket span=1h _time
| stats count by _time dstip
実際に実行するとこうなります。
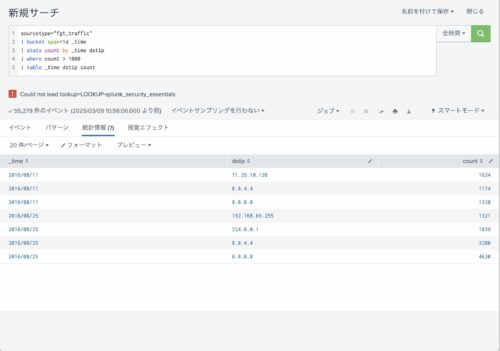
さらに、1時間で1,000回以上のアクセスがあったdstipを抽出するには以下の通り記載します。
sourcetype="fgt_traffic"
| bucket span=1d _time
| stats count by _time dstip
| where count > 1000
| table _time dstip count
こちらも実際に実行すると以下の通りとなります。
参考サイト:
・コアラでもわかるSplunkシリーズ 時間毎集計する(Qiita)
https://qiita.com/toshikawa/items/8fa44753bc8f2a4c9cb0
先日、神奈川の弘法山と権現山に行ってきました。
弘法山の駐車場は第1と第2駐車場があり、どちらも国道246号の「名古木宮前」という交差点をセブンイレブン側に入ってまっすぐいくと到着します。
実は最初、初めていく山だなと思いながら向かったのですが、到着してみるとなんだか見覚えがあるような、、、実は2回目の登山でした。
駐車場に到着後、まず最初は弘法山を目指したのですが、我々が車を止めた第2駐車場(10台くらい駐車可能、無料!)からはものすごく近くて、多分真っ直ぐ目指せば10分ぐらいで到着してしまいます。

この後、弘法山から権現山をめざしたのですが、このルートがお天気が良く、富士山も見えることもあって絶品でした。
ちょうど小さい公園の広場のようなところがあり、そこにさらにちょうど良い感じで長椅子があったので、そこに座ってコンビニのおにぎりを食べました。
もうそこはずっと座っていてもいいな、というくらい癒される空間でした。

その後、権現山に到着すると、そこは広い公園のような場所でした。また、そこにはバードウォッチングができる場所や展望台などがあり、多くの人がくつろいでいるようでした。

弘法山から権現山に向かうルートは道が整備されており(階段はコンクリート)そんなに急な坂道はない為、家族連れで訪れるには最高の場所だと思いました。
なお、残念ながらここの桜や河津桜ではないらしく(ソメイヨシノ?)まだ咲いていませんでしたが、3月末頃にくればきっと満開になっていることだと思います。
またその頃にきてみたいなと思っています。(でもその時は駐車場がいっぱいかな。)
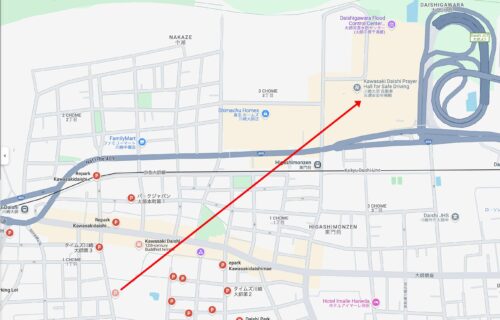
川崎大師 平間寺のすぐ横にある駐車場は、一見、誰でも車を駐車できそうですが、予約制になっていることがあるので注意が必要です。
特に年末年始は参拝者が多いので、予約制になっていると考えた方がいいと思います。
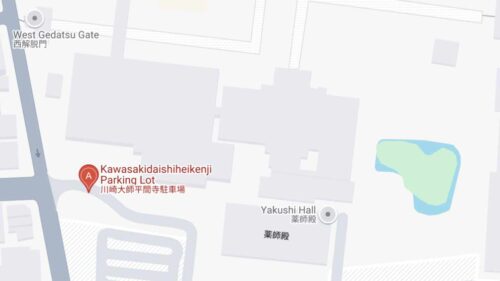
ここに行った後、川崎大師 自動車交通安全祈祷殿の駐車場に行こうとすると下図の通り道がややこしいので、最初から自動車交通安全祈祷殿の駐車場に行ったほうが無難ですし、大きな祈祷殿が目印になっていてわかりやすいです。
stats マクロで count を利用すれば、特定の項目の出現回数を表示させることができます。
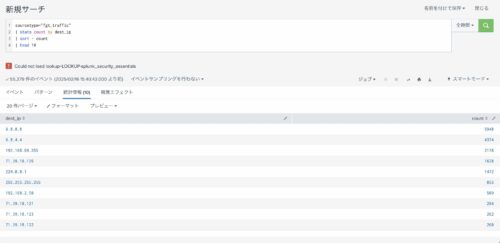
下記のSPLは、dest_ip(通信先)毎に出現回数をカウントし表示させるSPLの例です。
なお、それぞれのdest_ipの出現回数をカウントした後、カウントが多い順に10件表示しています。
sourcetype="fgt_traffic"
| stats count by dest_ip
| sort - count
| head 10
実際に実行するとこうなります。
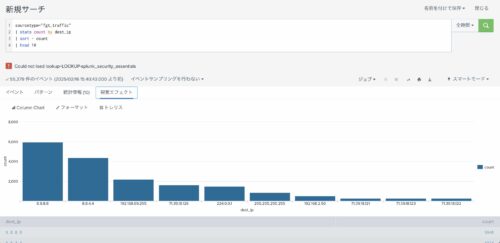
上記検索を行った後、「視覚エフェクト」を選択すると、結果をグラフ表示することも可能です。
参考サイト:
・Splunk: Splunk入門(SPL編 3/6) – よく使用する統計関数11選
https://qiita.com/frozencatpisces/items/360b4a38212fe1876dbc
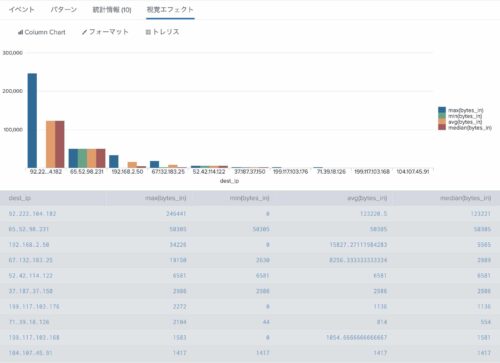
stats マクロで avg と median を利用すれば、特定の項目の平均値と中間値を表示させることができます。
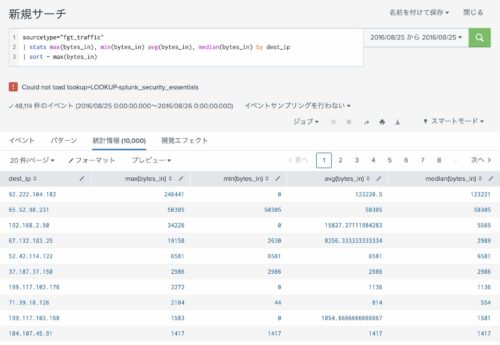
下記のSPLは、dest_ip(通信先)毎に最大値(max)、最小値(min)、平均値(avg)、中間値(median)を表示させるSPLの例です。
なお、それぞのれ値を求めた後、最大値(max)が多い順番に並べ替え、最大値(max)が多い順に10件表示しています。
sourcetype="fgt_traffic"
| stats max(bytes_in), min(bytes_in) avg(bytes_in), median(bytes_in) by dest_ip
| sort - max(bytes_in)
| head 10
実際に実行するとこうなります。
上記検索を行った後、「視覚エフェクト」を選択すると、結果をグラフ表示することも可能です。
参考サイト:
・Splunk: Splunk入門(SPL編 3/6) – よく使用する統計関数11選
https://qiita.com/frozencatpisces/items/360b4a38212fe1876dbc
先週あたりから Mac にインストールしている Avira Free Security がHTML/ExpKit.Gen6というマルウェアを検知し始めたようなので、削除してみました。
おそらく FireFoxであるサイトにアクセスしたことで危険なHTMLがダウンロードされたようで、FireFoxを起動するたびにAvira Free SecurityがHTML/ExpKit.Gen6を検知していました。
そこで以下の手順で対応しました。
1.Arcブラウザをインストールし、FireFixのブックマークをインポート
2.FireFoxをアンインストール
3.Aviraにて隔離されているマルウェアを削除
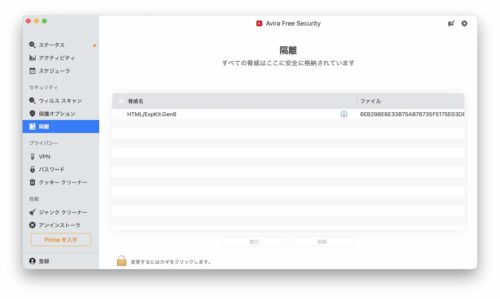
今回は3.の「Aviraにて隔離されているマルウェアを削除」する方法を簡単に説明します。
Aviraで隔離されたファイルの一覧が表示されます。
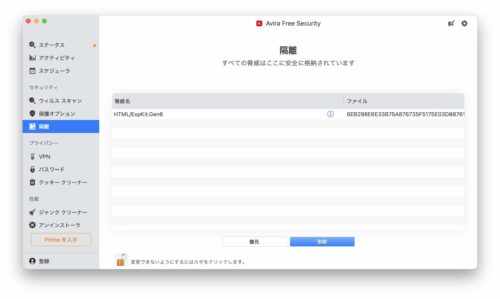
ロックを解除するとファイルが選択できるようになります。
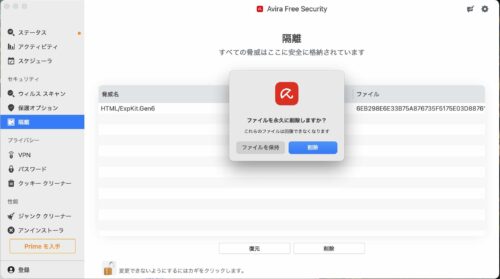
3.2で選択したファイルが削除できます。
stats マクロで特定のフィールドの値の出現回数をカウントし、それを sortマクロで多い順に並べ替えることで実現できます。
index="(インデックス名)" sourcetype="(ソースタイプ名)" (フィールド名)=(カウントしたい値)
| stats count by (カウントしたいフィールド名)
| sort - count
(カウントしたいフィールド名)に src_ip や hostname など、カウントしたいフィールド名を入れます。
なお、1行目は index 以外は任意(必須ではない)です。
また、”|”は半角になっている必要があるので注意。(全角にすると”|”が緑色になります。)
詳細は省きますが、先日、お葬式を実際に行ってみてわかった段取りと実際にかかる費用をここにまとめておきます。
朝、7:47に亡くなったため、8:30頃にあらかじめアテをつけていた葬儀屋(O会館)さんに電話しました。
その後、10:00に亡くなった病院で葬儀屋さんと待ち合わせをし、そのまま葬儀屋さんの遺体安置室へ。
10:30から葬儀屋さんの応接室で打ち合わせをし、その後のスケジュールは以下のとおり。葬儀屋さんが手書きで書いてくれました。

明け方亡くなった為、その日の夜にもうお通夜をしました。
突然の連絡で、また、実家から離れた病院のある町だったので、流石にその日の夜に駆けつけてくれる人はいないかともおもいましたが、お2人ほど、遠方から車でわざわざ駆けつけていただきました。
その2人が帰られた後は、葬儀屋さんの控室で寝ました。浴衣はありませんでしたが、ホテル並みのユニットバスがあったのは助かりました。
朝、目が覚めた時最初に思ったのは、昼間の仕出し弁当がたりないかもしれない!ということでした。
昨日のお昼すぎに親戚に電話したので、あまり来れないのではないかと思い少なめの数にしていましたが、とてもありがたいことですが、予想もしなかった人がお別れに来てくださることになったので、すこし足りなくなりました。
そこで自分たちは最悪コンビニ弁当で数を調整できるように、明け方、3つのお弁当を買い出しにいきました。
結果的に仕出し弁当が2つ足りない事態にはなりましたが、コンビニ弁当のおかげで急場をし退くことができました。
仕出し弁当は急に数を増やせないので、すこし多めに手配しておくことがじゅうようですね。
10時からの葬儀、出棺、火葬はたんたんと行われ、再度、葬儀屋さんの会館にもどり、初七日を行いました。
なお、葬儀にきていただいた方にはご香典をいただいた際にお車代とお礼(コメダのセット)をお渡しし、遠方からきていただいたお坊さんにも(たしか、葬儀の少し前だったとおもいますが)お布施とお車代をお渡ししました。
そういえば、初七日のあとは、三日目にお寺にもっていく4点セット(後述)と3段になった簡易祭壇(段ボール製)をアパートまで葬儀屋さんにもってきていただきました。
この日はお葬式で祭壇に飾られていた以下の4点セットをお寺に持参し、お祈りしていただきました。
1.遺影(写真)
2.位牌(小さい方のみでよいですが、念の為大きいのと両方)
3.塔婆(とうば)・・・長い板
4.遺骨(骨壷)
本当は、祭壇に飾られていた花の一部を前日に受け取っていたため、それも持参しておくとよかったかもしれません。
お祈りの際は、おそらくお坊さんが連絡してくれていたのだと思いますが、まわりの集落の方がお別れにきてくれました。
このときにもご香典をいただいたのは予想外でしたが、49日にまたお寺をおとずれた際に、お返しをしようと思っています。
そして、初日、二日目の病院からの搬送と初七日完了までにかかった費用は以下のとおりです。実際にはこれにプラスして消費税がかかった+昼間の仕出し弁当は別なので、80万と少しという結果となりました。
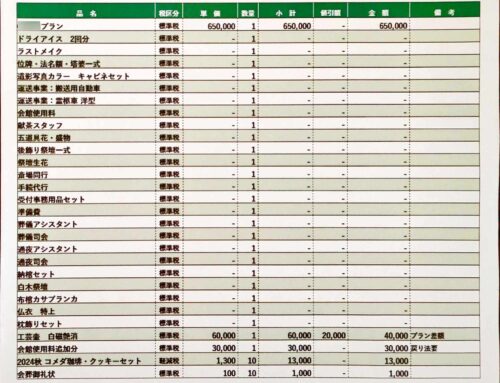
なお、葬儀屋さんにお支払いしたのは以上ですが、そのほかに、
・お布施代
・お車代
などは別にかかっていますし、自分たちのホテル代や交通費、レンタカー代などもかかりましたので、トータルだとなんだかんだで140万円くらいはかかってたのではないかと思われます。
やはりお葬式はお金がかかるものなのだなぁを実感しましたが、いろいろ人も動いてくれ、段取りもちゃんととってくれたので、葬儀屋さんの費用は適正だったかなと思います。
もっとやすいプランもありましたが、それだといろいろ足りないものがでてくる、もしくはよくわからないなかで自分たちで段取りしないといけない、となっていたと思います。
結果的に、必要最低限のものがすべてそろっていた今回のプランが妥当かとおもいました。
もし突然、親族がなくなってしまって何も段取りができてなかったとしても、最低限、よさそうな葬儀屋さんの当てをつけておくことは大事だなとおもいました。
そういえば、よくある話ですが、葬儀屋さんの会員になりましたので、時間は葬儀代が10%引きになるそうです。
名前からしてコスト重視のビジネスホテルのように感じられますが、それだけではなかったです。スーパーホテル山口湯田温泉

まず、Welcome Bar というサービスがあり、なんと、地酒やワインなど10種類を超えるアルコールが夜9時までただで飲めます!
さらに、湯田温泉だけあって「白狐の湯」という大浴場に入れます。
そして朝は、健康志向の朝食がバイキング形式で食べられます。その中にはホテルオリジナルのパンや卵かけご飯などあり、とても平日10,000円以下で泊まれるホテルとは思えないです。
また、ホテルの従業員もとても礼儀正しいので快適に宿泊できることまちがいなしなので、ぜひ一度泊まってみてください。